In this tutorial, we will understand Linux Password policies for Stronger password requirements.
Have you ever thought about why it is important to follow password policies or to create a stronger password? Folks, there are a lot of hackers and crackers around us. We never know when our system would get hacked or some important information got stolen. Anything can happen! Most of the people set weak passwords or reuse their old passwords.
According to an article published on entrepreneur.com, 91% of the people know that reusing passwords is a poor practice, and you know what 59% of the people reuse their passwords everywhere. People should understand why it is important to have a safe and strong password. In 2013, Adobe reported that hackers had stolen nearly 3 million encrypted card records, plus login data for an undetermined number of user accounts. You can see the most reputed firms aren’t safe, Therefore it’s our duty to have precautions.
That’s why I thought to give a word regarding Linux Password policies for stronger password requirements. There are a total of 9 password policies that Linux had made for the users. These are:
- Minimum password age policy
- Maximum password age policy
- Password History policy
- Minimum password length policy
- Use uppercase characters policy
- Use lowercase characters policy
- Using minimum digits in the password policy
- Password warning policy
- Password retry policy
We will discuss all the examples based on a user. Let’s first add the user by using adduser command in the CLI. This will add the user to the system. Let’s have a look at the command:
sudo addusr vaishali
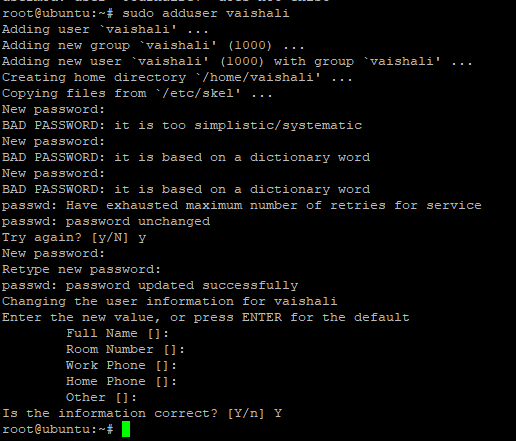
If you use a simple dictionary word password, you might see errors like “too simple” or “based on a dictionary word”. See, the system already knows you are using a very weak password. The system wants to protect your data! So set your password wisely.
Let’s discuss in detail about each policy.
Linux Password Policies – Minimum Length Policy
This policy improves password security by setting a minimum length. We have the tendency to set easier passwords so that we could remember them easily. But this sets a threat to our data. Do you want that your passwords should be easily cracked by the crackers? I don’t think so! No one wants this. By default, there is a length fixed for the passwords in the Linux system. We can change that length too. Let’s learn more about this.
What if we want to add more functionalities to the password like it must contain uppercase or lowercase character, should be of length 12 character. This can be possible but make sure you have installed the password quality check library. If not, don’t worry folks, you can use the apt command below to complete the installation. Let’s have a look:
sudo apt-get install libpam-pwquality
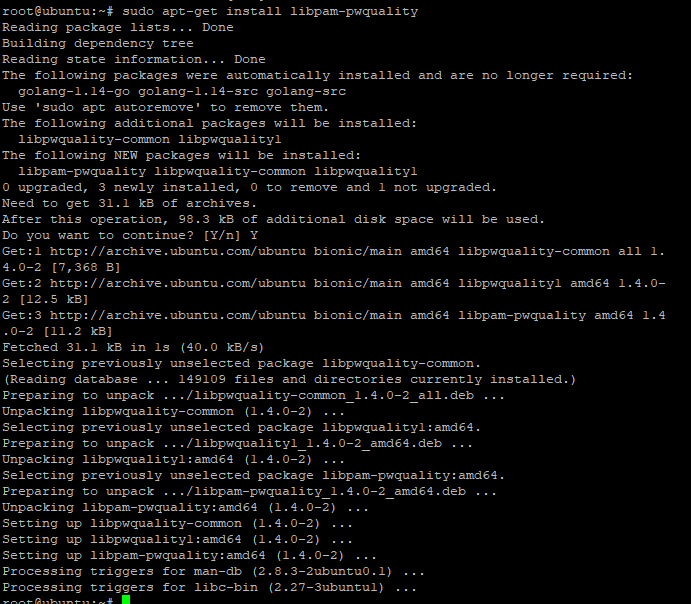
Now, we need to use the common-password file where we can add the functionalities. The common-password file is located in /etc/pam.d directory. Here, below I have provided the command to access it:
cd /etc/pam.d
ls
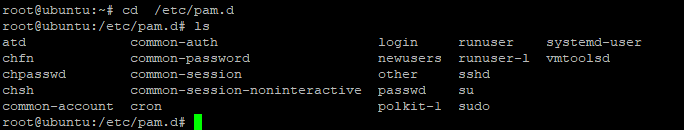
Use the ls command to list all the files. You would see a file named common-password. Open the file using nano command as shown below:
sudo nano /etc/pam.d/common-password
The text-editor will open where you would find the code. Here, we can set up Linux password policies like the minimum length. To add the minimum length as 12, use minlen=12 at the end of the first non-commented line (see the first white line below.
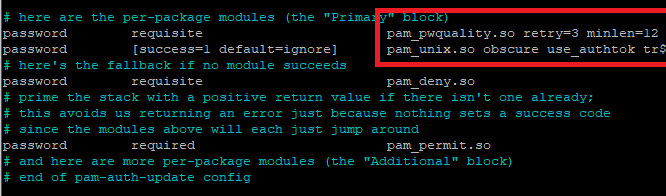
Don’t forget to save the file. Use Ctrl + O to save the change and then exit the editor using Ctrl+X. If you again try to change the password, the changes will be reflected. In the below image, you can see I tried to set the password of length less than 12 but it displayed the error.
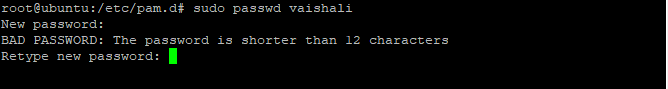
I hope you understood this.
Password History Policy
Let’s move on to some more settings for the Linux password policies. We’ll set the password history policy here. Have you ever noticed, while changing your google password if you use any of your old passwords, it notifies that this password has been used before? It checks the history of your password. This is the same as Linux’s password policy. When the user sets a new password or change his password, it will check it against all the passwords and if it matches, it will show a message.
If you want to set this functionality, can do so by changing the remember parameter in /etc/pam.d/common-auth file. I have discussed above how to list all the files located in pam.d directory. You would find a file named common-auth where you can set the remember parameter to any value you want. You can access the file using the command as shown below:
sudo nano /etc/pam.d/common-auth
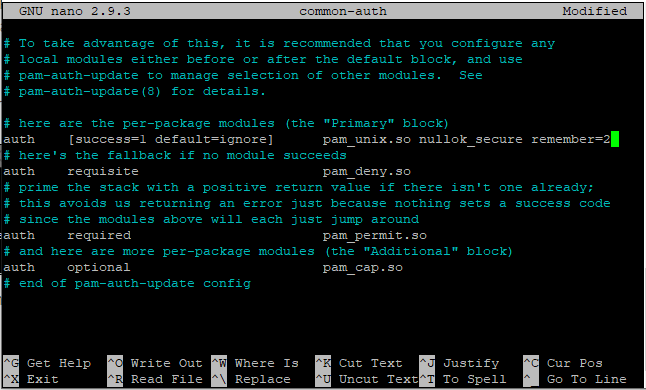
Here, I have set the value to 2 i.e. the user won’t be able to use any password which matches his last 2 passwords used.
Setting the Maximum Life of a Password
Seems interesting? Yeah! Till now we discussed how to set number historical checks. For a user, we can set a max period until we will be able to use this password. This is one of the important Linux password policies so make sure you implement this one without fail.
If you the same password for a longer period of time, it might get hacked. Therefore, you should change your passwords regularly. You can change the maximum number of days of the password in login.defs file. This file is located in /etc directory. I have provided the command below to open the file. You can change the value of parameter PASS_MAX_DAYS. This functionality is called Maximum Age Policy. Let’s have a look at the command:
sudo nano /etc/login.defs
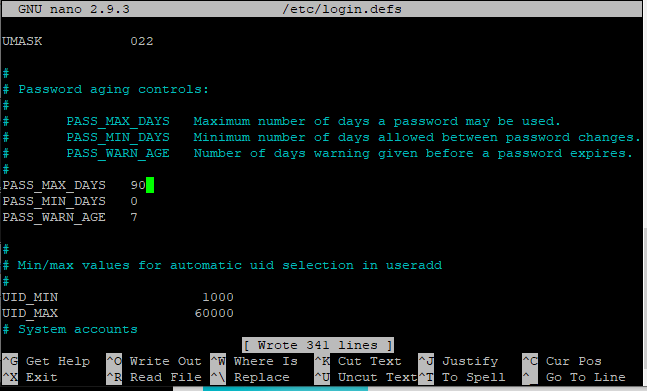
Change the value of PASS_MAX_DAYS, save changes and exit the editor.
Minimum life of Password
Now, you would get the point that I want to discuss. Earlier, we discussed the Maximum Age Policy. The Minimum age policy also sounds the same but with a small difference. In this, we are providing the age to the password, after a certain period it will get automatically expire.
Therefore, the user has to set the password again! For example, if I have set the maximum password age to 90 days, after 90 days the password will automatically expire. Notifying the user to set the new password. This attribute is located in the login.defs file which is present in /etc directory. Both the attributes i.e minimum age and maximum age are located in login.defs file. I have already provided the command to access the login.defs file. Below, I have provided it again:
sudo nano /etc/login.defs
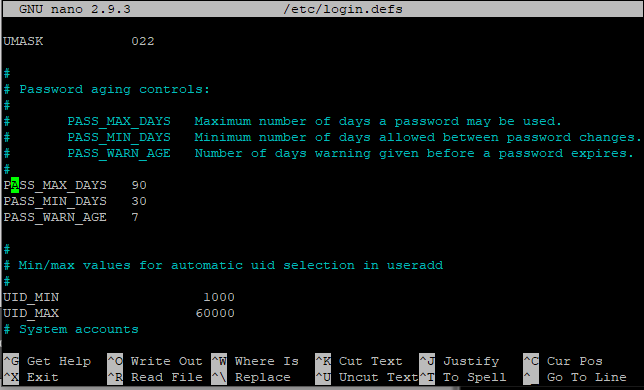
Here, you can set the value of PASS_MIN_DAYS as per your choice. Save the changes by using Ctrl + O as discussed above and exit the file.
Linux Password Policies – Password Warnings
You might be thinking of how a password can warn us? Be cool, it just shows the warning that the password you set before is going to expire and you need to change it.
Let’s have an example: When creating Linux password policies for your system, suppose we have set the maximum age of password to 90 days. So two or three days before, the user would get the prompt that your password needs to be changed before expiration. So, this attribute sets the reminder to change the password before the expiry date. This attribute is located below the minimum age attribute in login.defs file, located in /etc directory. Let’s have a look at the command below to open the file:
sudo nano/etc/login.defs
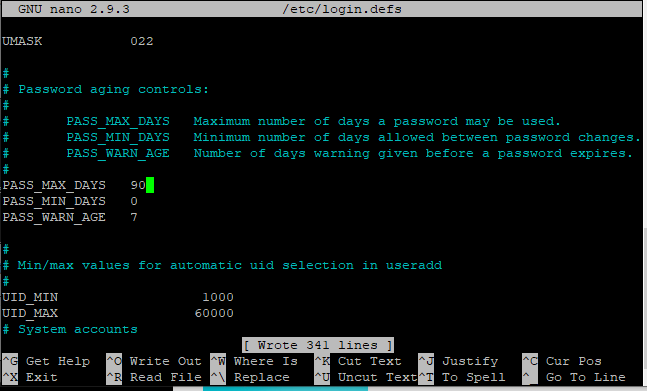
Set the value of PASS_WARN_AGE as per your choice. Let if you changed the value to 7, so it will remind you 7 days before the expiry of the password. Save the changes and exit the editor. Your changes will be reflected.
Allowing Passwords With a Minimum Set of Uppercase Characters
Yes! When creating Linux password policies for your system, you can also set the minimum uppercase characters that a password needs. Here, you can set the limit that how many uppercase characters can be used. This can be done by setting the value of ucredit. You have to set this option in a common-password file located in /etc/pam.d directory. Let’s discuss the command to open the file:
sudo nano /etc/pam.d/common-password
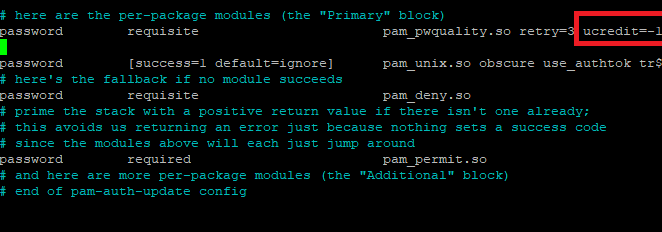
Here, you have to set the value of ucredit=-1. If you want to see the results, you can use the password change command as shown below:
sudo passwd vaishali
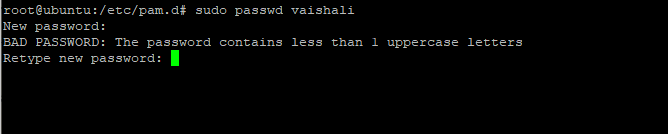
It will show the error that the password contains less than 1 uppercase letters. I hope you understood this policy.
Minimum Lowercase Characters
Earlier, we discussed how to set the minimum numbers of uppercase characters. You might be thinking that if there is an option to set the limit to uppercase characters, then there must be an option for lowercase characters too.
Yes! We have an option. Just replace ‘u’ by ‘l’ in ucredit. You have to set the value of lcredit to -1. You have make the changes in common-password file, located in /etc/pam.d directory. I have already discussed the path to pam.d directory. But don’t worry folks, I will discuss here too. So the command for this is as follows:
sudo nano /etc/pam.d/common-password
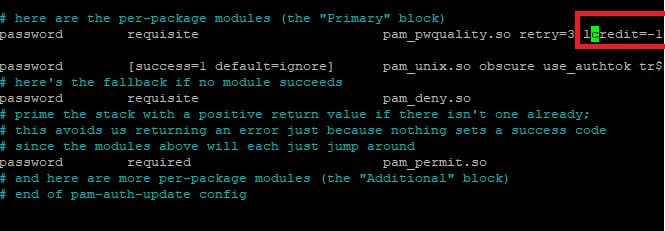
Here, you can see the value of lcredit is set to -1 which means we need at least 1 lowercase character. Save the changes and exit the text editor. It would reflect when you will again change the password using passwd command as discussed above.
Set a limit to digits in password
Yes! there is an option too to set the minimum digits in the passwords. Simply set the value of dcredit to -1 or any other negative number that you want to set as the minimum. Similarly, as we did above set the value of this attribute in a common-password file, located in /etc/pam.d directory. Let’s discuss the command for this:
sudo nano /etc/pam.d/common-password
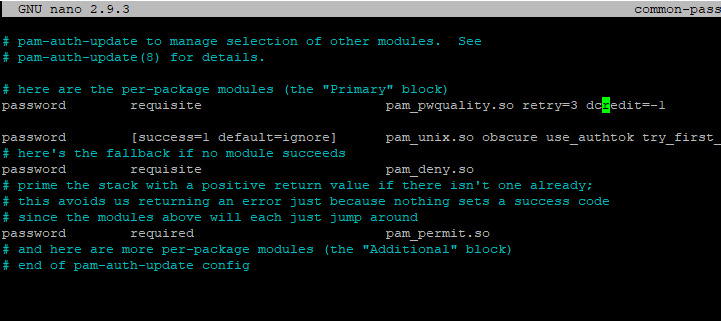
Here, we have to set the value as you see in the image shown above. Don’t forget to save the changes and exit the editor.
Linux Password Policies – Retry Limit
You might have seen while filling the password, if you insert the wrong password, again and again, it shows the message that you tried to the maximum attempts. But you can change the limits too!
You can set the value of retry as per your choice. Set this option in the common-password file located in /etc/pam.d directory. Let’s discuss the command for this:
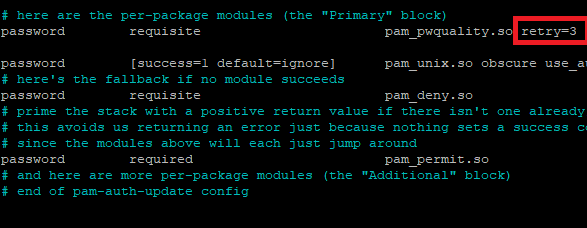
Set the value of retry as you want. Save the changes and exit the editor. I hope you understand the concept.
FAQs
Q: What are the basic requirements for a strong password in Linux?
A: A strong password in Linux typically involves a combination of upper and lower case letters, numbers, and special characters. It should also have a minimum length and should not be easily guessable.
Q: How can I set password complexity requirements in Linux?
A: You can set password complexity requirements in Linux using the password requisite pam_cracklib.so or pam_unix.so modules that enforce rules for password strength and complexity.
Q: What are the common password policies in Linux?
A: Common password policies in Linux include enforcing password expiration period, minimum password length, preventing password reuse, and setting password strength requirements.
Q: How can I set password expiration in Red Hat Enterprise Linux (RHEL)?
A: In RHEL, you can set password expiration period using the pam module by configuring the days before password expiration parameter in the system’s PAM configuration.
Q: What is the PAM module for enforcing password policies in Linux?
A: The Pluggable Authentication Module (PAM) is used for enforcing password policies in Linux systems by providing a flexible and modular approach to authentication.
Q: How can I prevent users from reusing old passwords in Ubuntu?
A: To prevent users from reusing old passwords in Ubuntu, you can configure the password requisite pam_cracklib.so module to enforce this policy.
Q: What is the recommended approach for managing password policies in Debian and CentOS?
A: The recommended approach for managing password policies in Debian and CentOS is to use PAM configuration to enforce password complexity, expiration, and other policies.
Q: What are the best practices for setting password expiration periods in Linux?
A: It is recommended to set a reasonable password expiration period in Linux, ensuring that users are required to change their passwords after a certain number of days to enhance security.
Q: How can I enforce a complex password policy in Linux to mitigate brute-force attacks?
A: You can enforce a complex password policy in Linux by using PAM modules to require strong and secure passwords, including the use of special characters and a minimum password length.
Q: What are the guidelines for creating secure passwords in Linux systems?
A: The guidelines for creating secure passwords in Linux systems include using a combination of upper and lower case letters, numbers, and special characters, as well as avoiding easily guessable passwords.
Conclusion
We have successfully discussed the Linux Password policies to set a stronger password. If face any issues, then do let us know in the comments section.