Linux is known for being a secure operating system, but out-of-the-box security is not enough for most production environments. Strong security comes from properly managing access control, using the right firewall tools, and monitoring system activity. Linux gives you powerful built-in tools like ufw, firewalld, and iptables for managing firewalls, and advanced frameworks like SELinux and AppArmor to enforce access policies. Tools like auditd help you log and review system-level events, adding a final layer of accountability.
This guide introduces the essential parts of Linux system security: how firewalls work, how to secure user accounts, what SELinux and AppArmor do, and how to audit logs. You will also learn practical security best practices, keeping your system safe in real-world use cases.
Managing Firewalls: ufw, firewalld, and iptables
A firewall controls incoming and outgoing network traffic. In Linux, there are multiple tools to configure firewall rules, and each suits different use cases.
UFW: Uncomplicated Firewall
ufw is a user-friendly command-line tool for managing firewall rules. It is often used on Ubuntu and Debian-based systems.
To enable the firewall:
sudo ufw enable
To allow SSH access:
sudo ufw allow ssh
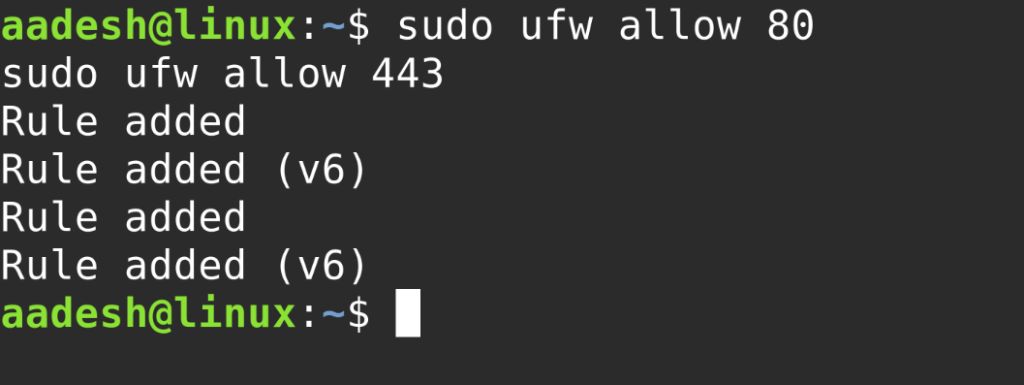
You can also allow specific ports, such as HTTP (port 80) or HTTPS (port 443):
sudo ufw allow 80
sudo ufw allow 443
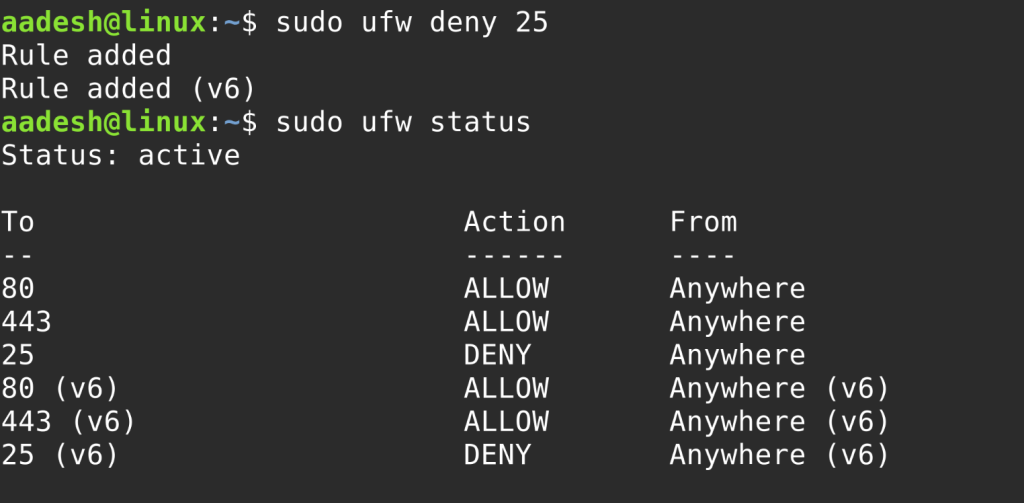
To deny or block a port:
sudo ufw deny 25
To check the current status and rules:
sudo ufw status
This tool is good for beginners or for small servers that need simple rules.
firewalld: Dynamic and Zone-Based Firewall
firewalld is used on many Red Hat-based distributions like Fedora and CentOS. It provides a dynamic way to manage firewall rules using zones, which group interfaces and rules together.
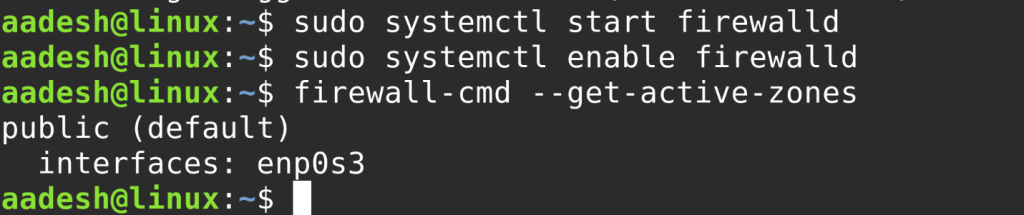
Start and enable the service:
sudo systemctl start firewalld
sudo systemctl enable firewalld
To view active zones:
firewall-cmd --get-active-zones
To allow HTTP service permanently:
sudo firewall-cmd --permanent --add-service=http
sudo firewall-cmd --reload
firewalld is more flexible than ufw and supports runtime rule changes without restarting services.
iptables: The Legacy Command-Line Tool
iptables is the traditional firewall utility in Linux, offering complete control over packet filtering. It is extremely powerful but complex.
To view existing rules:
sudo iptables -L
To allow a port:
sudo iptables -A INPUT -p tcp --dport 22 -j ACCEPT
To block an IP address:
sudo iptables -A INPUT -s 192.168.1.10 -j DROP
Most modern systems now use nftables or wrapper tools like ufw and firewalld, but iptables is still useful in many setups and scripting environments.
Linux Account Security
One of the most overlooked parts of system security is account management. A poorly managed user account can become an entry point for attackers.
Start by auditing existing users on your system:
cat /etc/passwd
Check for any unnecessary accounts or accounts with /bin/bash as the shell that do not need interactive login access.
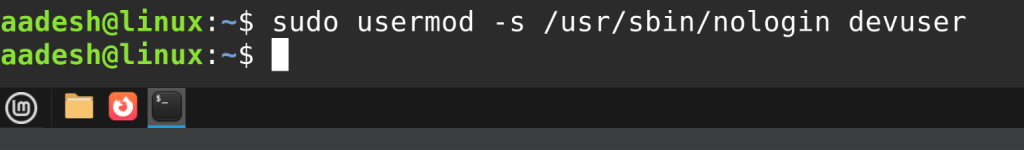
To disable login for a user:
usermod -s /usr/sbin/nologin username
Enforce password policies by installing libpam-pwquality or editing /etc/login.defs. Set password expiration, minimum length, and retry limits.
To lock a user account:
sudo usermod -L username
And to unlock:
sudo usermod -U username
Always use sudo instead of logging in as the root user. Restrict who can use sudo by editing the sudoers file:
sudo visudo
This file controls administrative access and should be limited to trusted users only.
SELinux Basics
SELinux stands for Security-Enhanced Linux. It is a mandatory access control (MAC) system used in Red Hat-based distributions. SELinux controls how processes interact with each other and with system resources beyond normal Unix permissions.
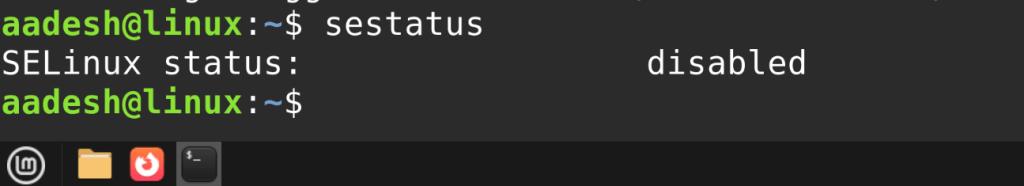
To check SELinux status:
sestatus
You will see whether it is enabled, and which mode it is in: enforcing, permissive, or disabled.
To switch modes temporarily:
sudo setenforce 0 # Permissive mode
sudo setenforce 1 # Enforcing mode
To change the mode permanently, edit /etc/selinux/config.
SELinux uses labels to manage access. Every file, process, and resource has a label that SELinux policies refer to. If a service fails due to SELinux, logs will appear in /var/log/audit/audit.log. Tools like audit2allow can help you interpret and resolve these errors.
Introduction to AppArmor
AppArmor is another security module similar to SELinux, used primarily in Debian and Ubuntu-based systems. It also uses profile-based access control to restrict what applications can do.
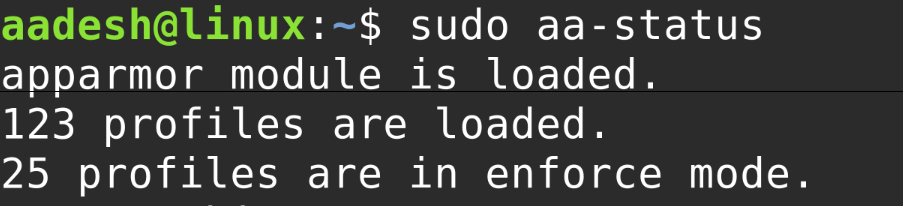
To check the AppArmor status:
sudo aa-status
Profiles define which files, capabilities, and system resources a program can access. You can find AppArmor profiles in /etc/apparmor.d/.
To load a profile manually:
sudo apparmor_parser -r /etc/apparmor.d/usr.sbin.mysqld
Unlike SELinux, AppArmor profiles are easier to read and write, but both serve the same purpose: preventing applications from performing unauthorized actions even if they are compromised.
Monitoring with auditd and System Logs
auditd is the Linux Auditing System daemon. It logs low-level system events such as file access, permission changes, and SELinux denials. It is often used in security-sensitive environments like servers and production infrastructure.
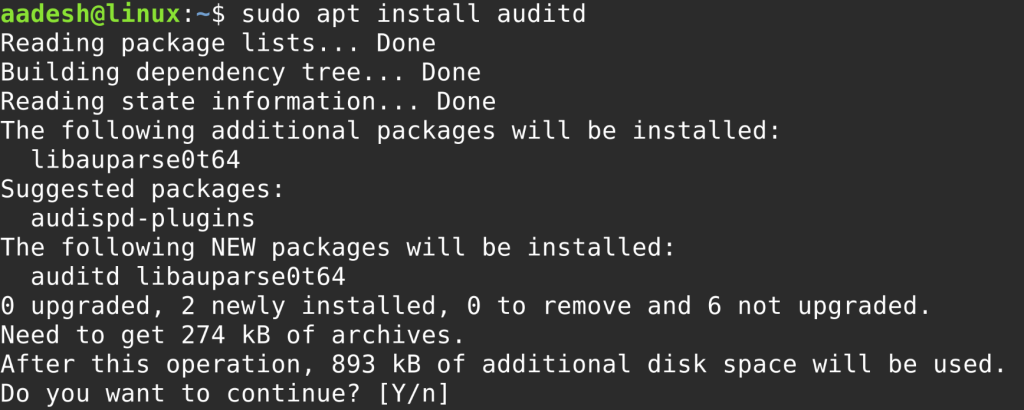
To install auditd:
sudo apt install auditd
Start and enable the service:
sudo systemctl start auditd
sudo systemctl enable auditd
To view recent audit logs:
sudo ausearch -x sshd
Or review full logs here:
sudo less /var/log/audit/audit.log
You can create audit rules to watch specific files or actions. For example, to monitor changes to the /etc/passwd file:
sudo auditctl -w /etc/passwd -p wa -k passwd_changes
This tells auditd to watch the file for write (w) and attribute changes (a) and label the rule with a key called passwd_changes.
Later, you can search for those events:
sudo ausearch -k passwd_changes
Auditd provides a detailed and tamper-proof way to track what is happening on your system.
Security Best Practices for Linux
Keeping a Linux system secure is an ongoing process. Start by following these simple best practices:
Always apply updates regularly. Use apt update && apt upgrade or your package manager’s equivalent to patch security flaws. Remove unused services, packages, and user accounts. The fewer components you have running, the smaller your attack surface.
Use SSH keys instead of passwords for remote logins. Disable root SSH access by editing the /etc/ssh/sshd_config file. Set PermitRootLogin no and restart the SSH service.
Enable and configure firewalls, preferably with ufw or firewalld, to block unwanted traffic. Audit your system regularly using tools like auditd, and review logs in /var/log/ to detect suspicious behavior early.
Limit sudo access, and enforce strong password policies. Consider enabling two-factor authentication (2FA) if possible for critical systems.
Combine traditional Unix permissions with tools like SELinux or AppArmor for layered protection. These systems prevent services from accessing files or resources they should not touch, even if the attacker gains access.
Summary
Linux offers a wide range of tools to secure your system and control who can access what. Firewalls like ufw, firewalld, and iptables help you manage incoming and outgoing traffic. Proper Linux account security ensures that users and services have only the access they need. SELinux and AppArmor take this further by enforcing mandatory access controls at the system level. Logging tools like auditd give you a complete trail of system activity so you can detect breaches early. Following basic best practices—like updating regularly, using SSH keys, limiting user access, and reviewing logs—can go a long way toward keeping your Linux environment secure. With these tools and habits in place, you are well-prepared to build and maintain a secure Linux system.