The netstat and ss commands in Linux are used to view open ports, active connections, and socket statistics on your system. These tools help system administrators monitor network activity, detect unauthorized access, and troubleshoot services that rely on network communication. While netstat is a traditional utility, ss is its faster and more modern replacement. Alongside these, hostname resolution is the process of converting domain names into IP addresses, allowing Linux systems to connect to websites and remote servers. Understanding these tools is essential for managing Linux network behavior effectively.
Using netstat to Monitor Network Connections
netstat, short for network statistics, is a legacy tool that provides detailed information about active network connections, listening ports, and routing tables. Although it is no longer installed by default in many distributions, it remains widely used and can be re-enabled easily by installing the net-tools package.
To begin using netstat, install it using the following command if it is not already available on your system:
sudo apt install net-tools
Once installed, you can use it to view all active TCP connections:
netstat -t
The -t flag limits the output to TCP connections only. To see both TCP and UDP connections with addresses and ports displayed numerically, use:
netstat -tun
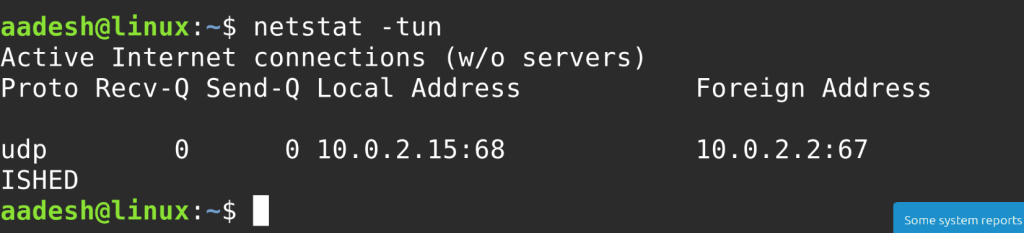
You can also check which processes are using which ports. This is helpful when diagnosing service conflicts or identifying potentially unwanted connections:
sudo netstat -tulnp
This command shows TCP and UDP sockets, lists which ones are listening, and maps them to process IDs and program names. However, keep in mind that netstat is considered outdated, and its modern replacement ss is recommended for current systems.
Why ss Replaces netstat
ss, short for socket statistics, is a faster and more powerful replacement for netstat. It is part of the iproute2 suite and is installed by default on most Linux distributions.
To view all listening sockets, use:
ss -l
If you want to see all connections (not just listening ports), run:
ss -a
To show which processes are connected to which ports, use:
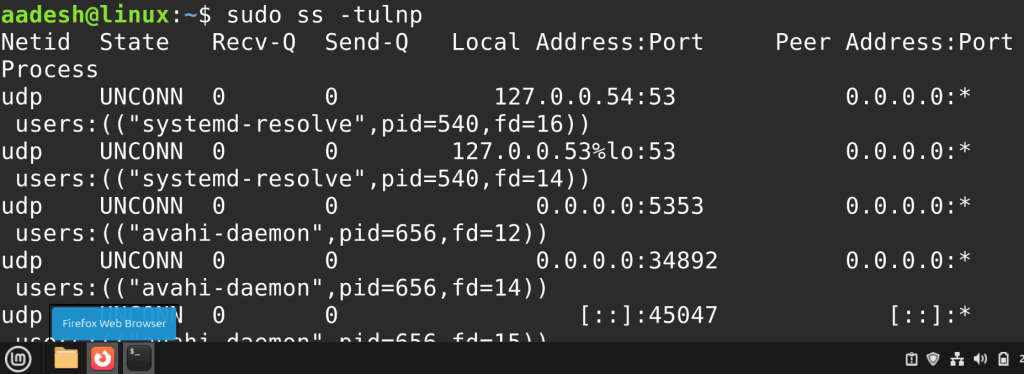
sudo ss -tulnp
This command is the closest equivalent to the one we saw earlier using netstat, and it gives detailed insights about both the program and the socket it is using.
The ss command executes much faster than netstat and offers better filtering options. For example, to filter only HTTP ports:
ss -tn 'sport = :80'
Or to check connections to a specific remote host:
ss dst google.com
ss supports expressions and selectors that make it ideal for advanced network diagnostics, especially on high-load servers or modern distributions where performance matters.
Understanding Hostname Resolution in Linux
Hostname resolution is the process of converting human-readable domain names, like example.com, into IP addresses that computers use to communicate. This process is managed by the system using configuration files and DNS queries.
When you enter a domain name, your system first checks the /etc/hosts file to see if there is a manual mapping. If it is not found there, the system queries the DNS servers listed in /etc/resolv.conf.
To view your current DNS configuration, open the terminal and run:
cat /etc/resolv.conf
This will list one or more nameserver entries, which are the DNS servers your system uses to resolve hostnames.
You can test hostname resolution using the ping or host command. For example:
ping example.com
or:
host example.com
If the system is unable to resolve the hostname, you will see an error message indicating that the domain name could not be found. This could be due to a misconfigured DNS server, a broken /etc/resolv.conf file, or restricted network access.
Another useful tool for detailed DNS queries is dig, which can show how the system resolves a hostname step-by-step. You can install it using:
sudo apt install dnsutils
And then run:
dig example.com
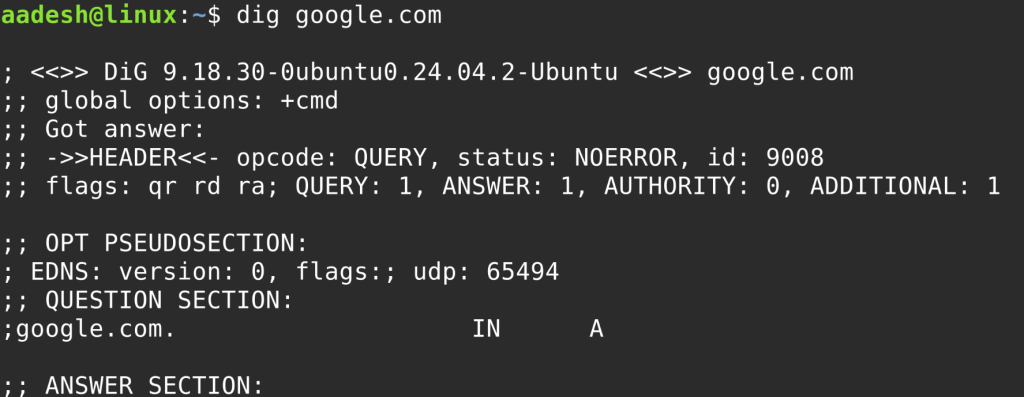
This will give you authoritative records, DNS lookup times, and IP address details.
Summary
Linux provides a range of tools to help you understand what is happening on your network. The netstat command, while older, remains familiar to many administrators and is useful for quick checks. Its modern replacement, ss, offers faster performance and advanced filtering that makes it ideal for today’s systems. Both commands let you see what ports are open, what programs are using them, and how your system is communicating with remote hosts.
At the same time, understanding hostname resolution helps ensure that your system can access domain-based services and websites properly. By using tools like cat /etc/resolv.conf, ping, host, and dig, you can troubleshoot and validate DNS behavior easily.
These tools are essential for daily Linux networking tasks and provide critical support when configuring servers, debugging services, or investigating suspicious traffic.