In this tutorial, we will see how to install and put anonsurf to use on Kali Linux. Initially, this powerful tool was purpose built for Parrot OS and now finally it has been made available to the Kali Linux users and other cybersecurity related Linux distros. In the recent articles, we discussed vulnerability scanning using Nmap and Nikto, Bluetooth spoofing using spooftooph, and OpenVAS.
While performing these scans or pen-testing, It is very important to hide your identity. We can hide our identity using a proxy or VPN. There is one more way to uphold our anonymity, i.e. using anonsurf. This tool can anonymize our complete system traffic tunneling via TOR using IPTables and thus keeps privacy in mind.
Tor network effectively conceals its user’s private information such as their device location and network details that the device is connected to from anyone who is trying to monitor the said user’s activity. Honestly, no one want their critical and private activity data to be exposed to adversaries.
Also read: How to install and use sherlock in Kali Linux?
How to run anonsurf on Kali Linux
Anonsurf was made by parrotsec which was ported to Kali Linux system by GitHub user Und3rf10w. This repo is a combination of resources from anonsurf and pandora packages. This application specifically is modified further to use Private internet Access DNS servers. The use of anon surf eliminates the need for using applications like tor browser. It also allows for the use of i2p, which is a fully encrypted private network layer.
I. Cloning the anonsurf repo in the local system
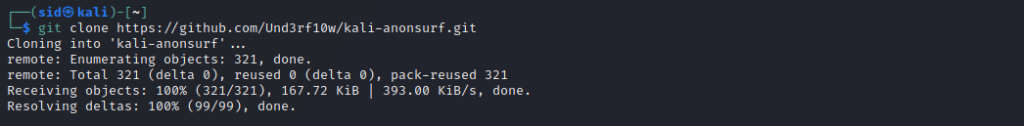
Open a terminal window by using Ctrl+Alt+T and clone it from the GitHub repository:
git clone https://github.com/Und3rf10w/kali-anonsurf.git
II. Installing anonsurf
Now, Change the directory to where anon surf is already downloaded by executing the following command:
cd kali-anonsurf/

III. Changing File permissions of the installed
Before we execute the installer, we need to change the file permissions using the following command,
chmod +x installer.sh
IV. Executing the installer
Then, install anonsurf using the command mentioned below. Press Y to confirm when prompted. This process will take few minutes, after which we should be able to keep our personal data clear off the prying eyes.
sudo ./installer.sh
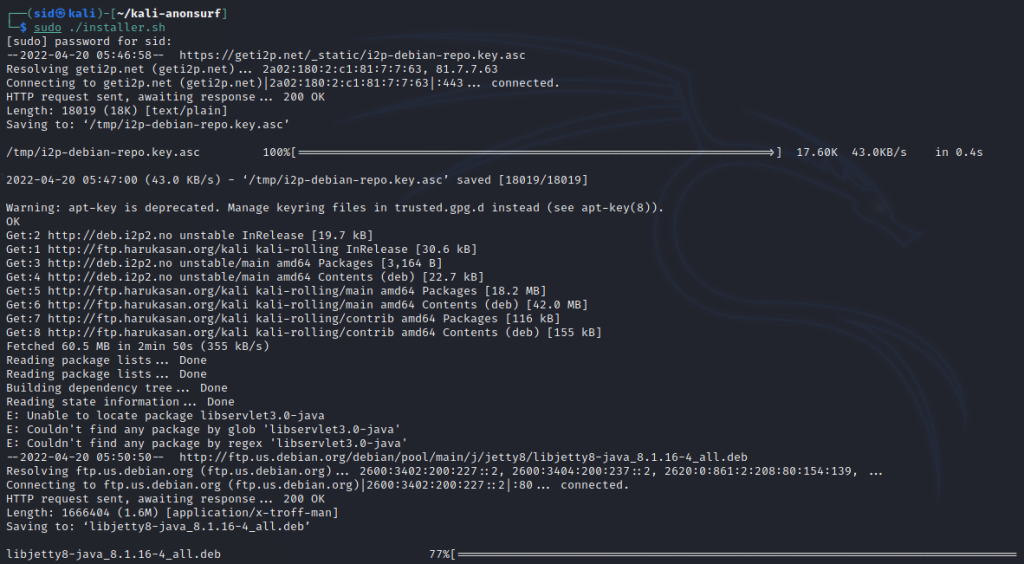
Hurray! Anonsurf is installed on our system. To check if the installation has succeeded, we can simply enter,
anonsurf
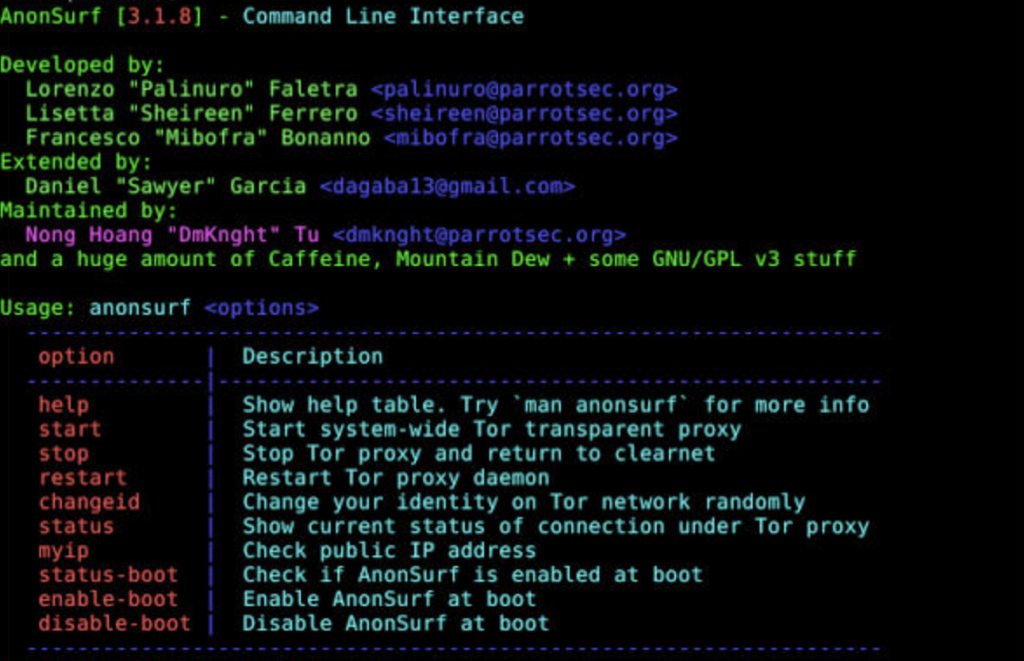
V. Working with various command options
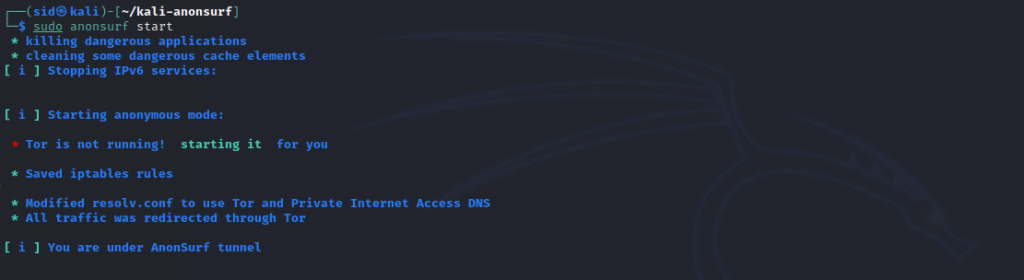
We can start anonsurf service in anon mode by running the following command:
sudo anonsurf start
Changing the identity using tor
What the change option effectively does is that it changes the tor circuit. Now, all the computer traffic through the tor network via 3 nodes by default, namely Guard, relay, and exit.
Depending on the flavour of the installation it could be sudo anonsurf changeid or just use
sudo anonsurf change

Checking the current IP address
To check your current IP address, execute the following command:
sudo anonsurf myip

You should see that running this command will change your IP address.
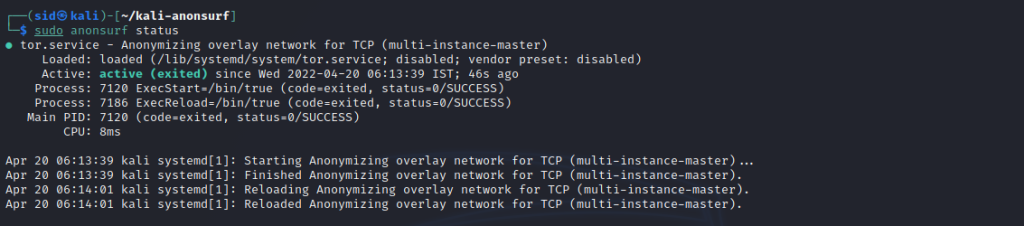
Checking the current status of the network
To check the status, run the command listed below:
sudo anonsurf status
Stopping the service
To stop the service, execute the listed below:
anonsurf stop

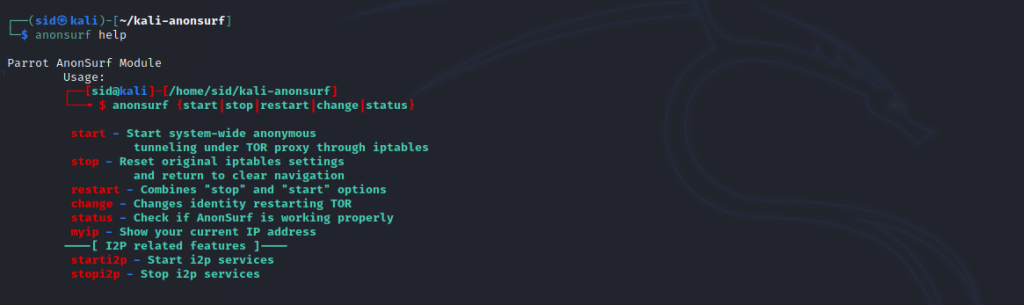
Read the man pages
To know more about this tool, You can refer to the help page by running the following command:
anonsurf help
Summary
We discussed how to install and use anonsurf to change our identity while doing pen-testing tests. But since we can never completely stay anonymous, this tool keeps us relatively more anonymous, and it is very useful for beginners as it automatically configures proxies. Tools like these enhance your privacy while you are trying to do ethical hacking or just penetration testing. Thank you for reading!
