Let’s learn about encrypting partitions with LUKS Disk encryption is a method of protecting confidential data and sensitive data on any storage device by converting the data into unreadable text (encrypting) such that only authorized users can decrypt and read the original data.
This method of protecting data is much stronger than simply having a password on your laptop since it actually changes the data itself instead of just putting it behind a password.
What is LUKS?
Linux Unified Key Setup (LUKS) is a disk encryption specification released in 2004 for Linux.
Since LUKS is a standard method and not an external software, its implementation is uniform across all distros, partitions, and even other block devices such a USB drives.
It uses multiple ciphers such as aes-cbc-essiv:sha256 and aes-xts-plain to encrypt the data. The specific cipher depends on the use case.
Step-By-Step Encrypting Partitions With LUKS
We will be implementing LUKS using the cryptsetup command. As an example, I will be encrypting my USB Drive. But this method can be used on any empty partition in Linux.
NOTE: Make sure you don’t have any data in the partition, USB you are going to encrypt as all the data will be lost in the process
Step 1: Identify the partition to be formatted.
You can list all filesystems using the following command.
df -hl
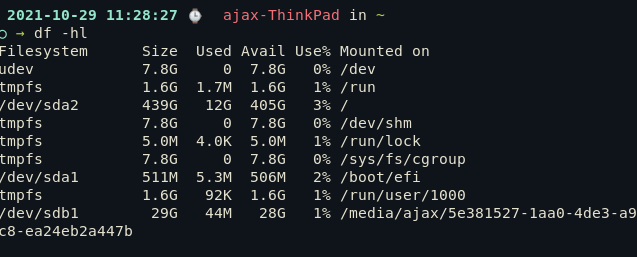
Since my USB drive is mounted at /dev/sdb1, I will be formatting that partition. If you formatting a primary hard drive partition this is usually something like /dev/sdaX
Step 2: Unmount the partition
sudo umount /dev/sdb1
Replace /dev/sdb1 with the name of your partition which we identified in the last step.
Step 3 : Format the partition
DO NOT RUN UNTIL YOU HAVE MADE SURE THAT THE PARTITION DOES NOT HAVE ANY IMPORTANT DATA
sudo wipefs -a /dev/sdb1
Step 4 : Format the partition with LUKS
Now we will use Cryptsetup on this formatted partition to make an encrypted LUKS partition. To do so, run the following
sudo cryptsetup luksFormat /dev/sdb1
After running this, you will be asked a passphrase. That passphrase is how you will access the device whenever you want. So make sure to remember the passphrase.
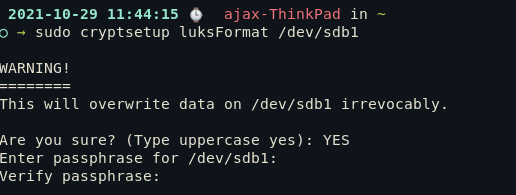
Step 5: Open the partition
Now your partition has a LUKS partition behind a password however it isn’t visible just yet.
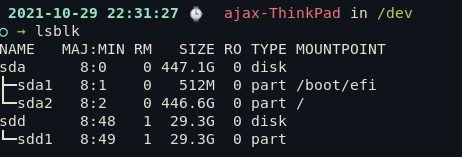
To access the encrypted Luks drive, execute the following:
sudo cryptsetup luksOpen /dev/sdd1 map_point
Here, you can replace map_point with any name that you like and the partition will be mapped to.
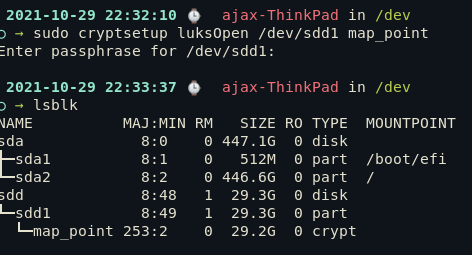
Now as we can see, lsblk shows the encrypted Luks partition (map_point).
Step 6: Create a filesystem in Luks partition and mount it.
Now to store files in the encrypted partition, we need a filesystem.
I will be creating an exFAT filesystem in the partition using the following command.
sudo mkfs.exfat /dev/mapper/map_point -n volume_name
You can choose any other filesystem. For ext4, use mkfs.ext4 and for FAT32, use mkfs.vfat, and so on.
Now that we have a filesystem, we can mount it to a location to access the contents.
mkdir /dev/luks_mount
sudo mount /dev/mapper/map_point /mnt/luks_mount
We are done with the implementation. Let’s see what do you need to do every time you need to access the data.
How to use LUKS?
If the partition you encrypted was on a USB drive, every time you insert the USB drive, you will be prompted with the passphrase to access the partition. The partition will be automatically mounted if you enter the password and can be accessed like a normal USB drive partition.
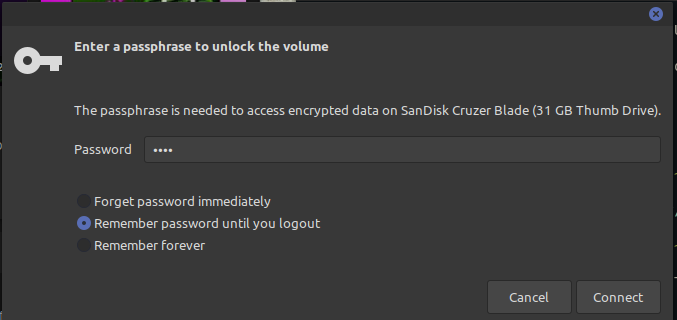
If you are not using a desktop environment, you will not get the GUI prompt and have to mount the partition itself using the commands below.
sudo mount /dev/mapper/map_point /mnt/luks_mount
ls /mnt/luks_mount
#Now you can access the partition at /mnt/luks_mount
#After you are done unmount and close the partition.
sudo umount /mnt/luks_mount
sudo cryptsetup luksClose volume_name
Conclusion
We have learned how to encrypt your partition and protect your sensitive data from the hands of unwanted users using Linux Unified Key Setup.
As with everything, it’s important to make sure to have a strong passphrase, have upper case characters, lower case characters, numbers, and special characters.
To read more about LUKS, head over to Redhat forums. Keep exploring!
