Today we’re talking about some of the less known Cyber Security Tools that I personally use very often! Cybersecurity is a vast field which requires a lot of tools for everything from enumeration to post exploitation kung-fu.
Top Cyber Security Tools You Wish You Knew Before
We all know about major security tools like nmap, metasploit, Burpsuite, etc. but in this module, we are going to study about 5 lesser-known, but instrumental tools which you wish you knew about sooner.
1. PEASS
PEASS – Privilege Escalation Awesome Scripts SUITE are scripts which help with the identification of probable post exploitation privilege escalation vectors.
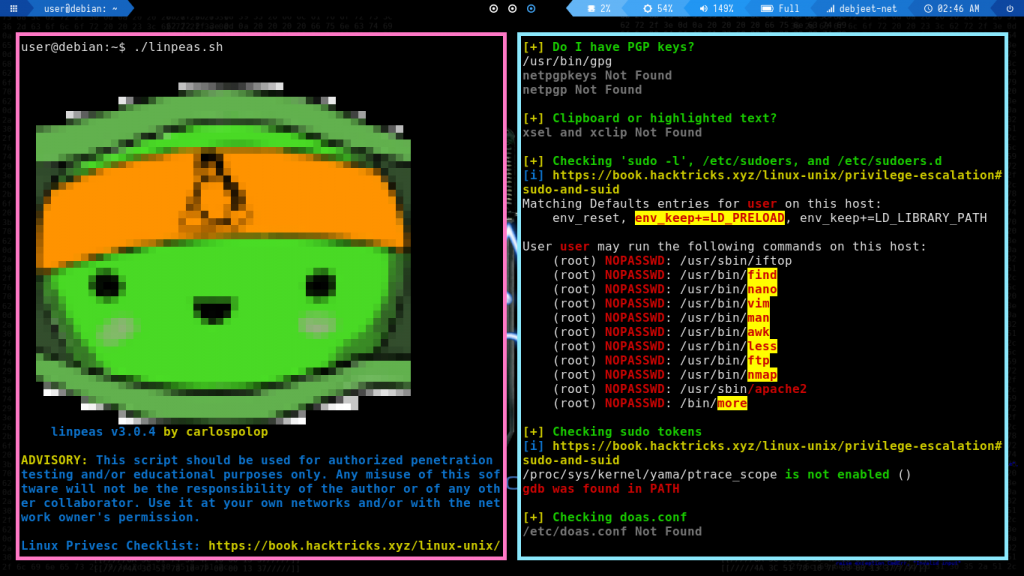
The most popular of PEASS is linPEAS which helps in the identification of various possible privilege escalation vectors on Linux/Unix type hosts. It is extremely instrumental when it comes to CTFs and even for audits. To use linpeas, transfer the script over to the machine you want to escalate your privileges on and run the chmod command:
$ chmod +x linpeas.sh
$ ./linpeas.sh
This should give you a summary of possible privilege escalation methods as such :
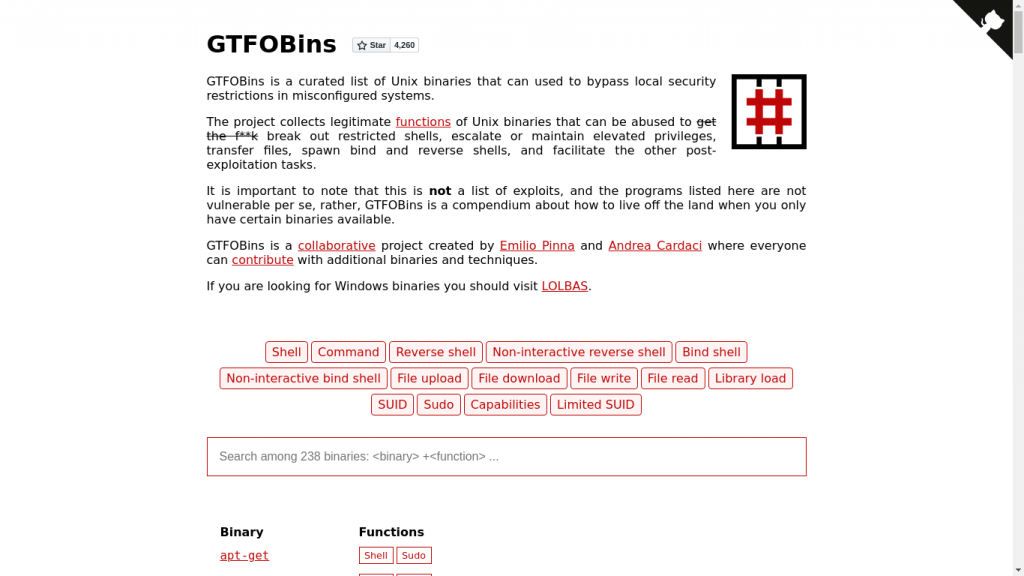
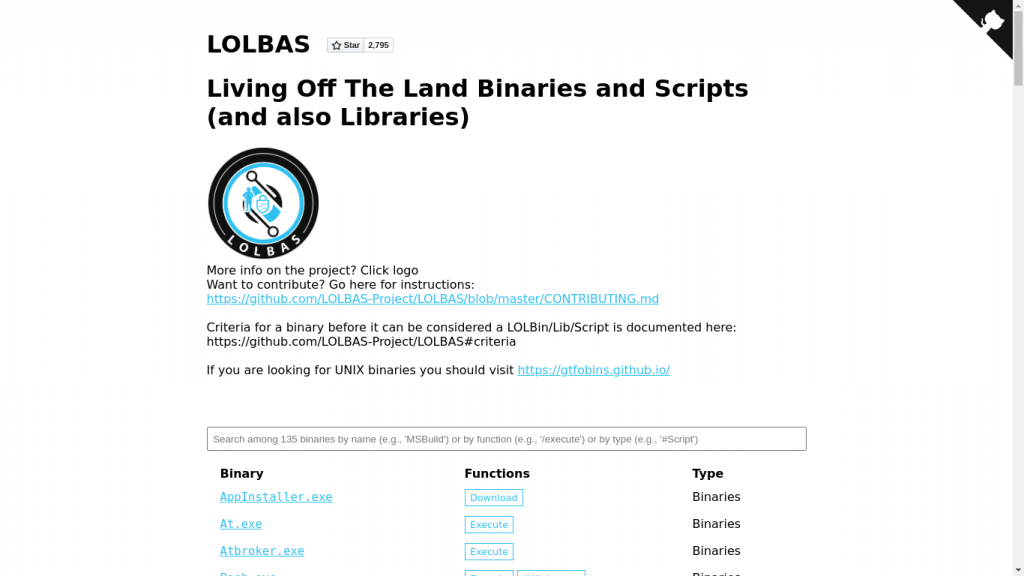
2. GTFOBins/LOLBAS
Next up we have GTFOBins for Linux/Unix* and LOLBAS for Windows which tell us how we can exploit special permissions on Binaries to escalate our privileges on a given system. Once you have found a Binary with special permissions, you can look them up here and it would suggest you a list of possible ways to exploit the same to gain root access !
3. Wordlistctl
This tool allows us to browse through a huge database of wordlists which can be fetched the ones we need according to our requirements. Originally a part of BlackArch, this tool can be fetched via it’s Github Repository.
Once you have fetched the tool on your system, you can search a wordlist by a keyword with:
$ wordlistctl search <keyword>
This gives you a list of all wordlists related to that keyword. For example, if you want to search for “rockyou“wordlists, you can type :
$ wordlistctl search rockyou
--==[ wordlistctl by blackarch.org ]==--
> rockyou-05 (104.00 B)
> rockyou-10 (723.00 B)
> rockyou-15 (1.94 Kb)
> rockyou-20 (4.00 Kb)
> rockyou-25 (7.23 Kb)
> rockyou-30 (12.16 Kb)
> rockyou-35 (19.65 Kb)
> rockyou-40 (31.22 Kb)
> rockyou-45 (49.13 Kb)
> rockyou-50 (75.91 Kb)
> rockyou-55 (115.19 Kb)
> rockyou-60 (170.24 Kb)
> rockyou-65 (244.53 Kb)
> rockyou-70 (344.23 Kb)
> rockyou-75 (478.95 Kb)
> rockyou-withcount (56.02 Mb)
> rockyou (53.29 Mb)
> rockyou-5 (104 B)
To fetch a wordlist, the syntax is :
$ sudo wordlistctl fetch -l <wordlist> -d
The downloaded and decompressed wordlist is stored at /usr/share/wordlists/ under the respective group folders.
4. Pwncat
Pwncat is often described as “netcat on steroids” as it comes with some powerful Reverse/Bind shell and port-scanning capabilities, IDS/IPS and Firewall evasion and self-injecting shells, and port forwarding. It is also fully scriptable with Python (PSE) which allows us to extend its functionality and modify it according to our needs.
It can be installed with:
$ sudo pip install pwncat
On Arch based systems, it can be fetched from AUR with :
$ paru pwncat
Pwncat shells are SIGINT aka “Ctrl+C” proof. Often shells break on receiving SIGINT but not with pwncat which provides advanced Bind/Reverse shell capabilities. A full list of capabilities can be found on Pwncat’s Github Repository.
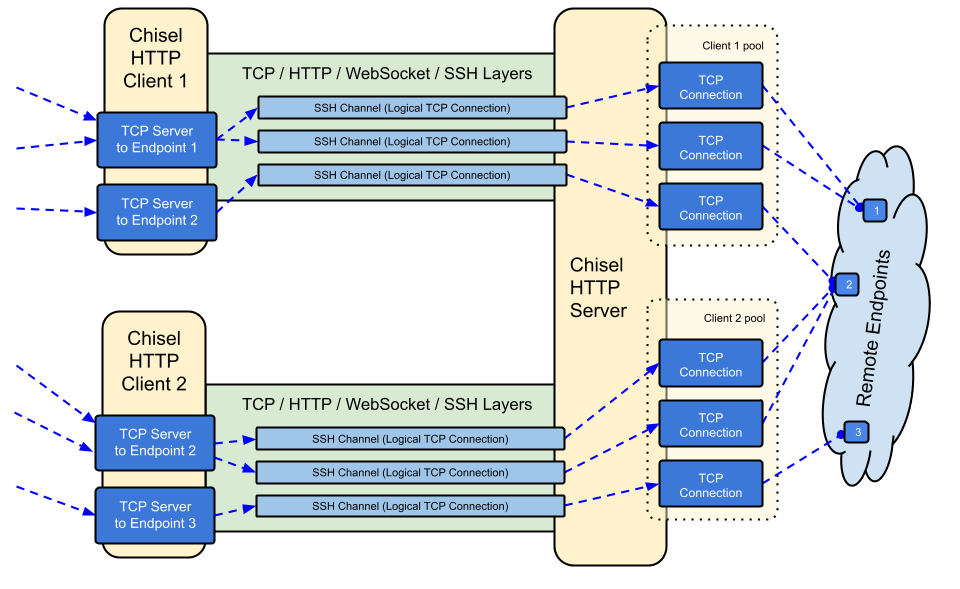
5. Chisel
Chisel is one of the fast cyber security tools for TCP/UDP tunnels, written in Golang, transported over HTTP, secured via SSH. It contains a single executable that contains both server and client modules. It is mainly useful for passing through firewalls, though it can also be used to provide a secure endpoint into your network.
Chisel can simply be installed with:
$ curl https://i.jpillora.com/chisel! | bash
The Github Repository discusses the functionality and usage in great detail. However, the following diagram describes the working of the binary in a very neat way :
Conclusion
These are some of the cyber security tools that are less talked of but extremely instrumental to both beginners and intermediate hackers. However, these tools must be used ONLY for educational purposes or on servers/domains one has permission to fuzz around.
