
Security is becoming increasingly important for many organizations. Therefore, before deploying any application, they will typically do threat modeling to understand the threats. For threat modeling to be effective, it must first identify the various kinds of threat agents that can harm an application or computer system. These threat agents can include things like the technologies currently being used and the input being provided by the users. It examines the situation from the point of view of malicious hackers to determine how much damage they are capable of causing and how dangerous the situation can become.
Threat modeling is performed as a part of DevSecOps, and that too by following the shift left approach during software development. By threat modeling, organizations can easily understand the threats and can place countermeasures within the application. Organizations are using different models; one such model is the STRIDE model.
Threat Modeling Using STRIDE
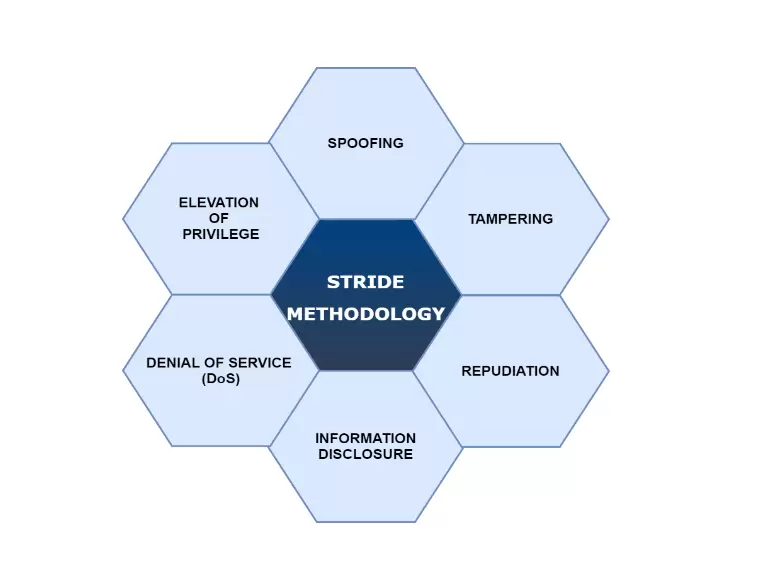
Threat modeling is the pinnacle of the shift left strategy and is mainly performed as a part of the DevSecOps strategy. It is possible to make use of it to identify and get rid of potential vulnerabilities before a single line of code is written as this is something that is done in the beginning phase of the development process. There are six different threat categories that STRIDE covers. Each character of STRIDE defines different threats.
Spoofing
Spoofing basically violates the principle of authentication. The spoofing of identity occurs when an attacker with harmful intent appears to be another person, such as by compromising a user’s username and password using phishing emails. As a result, this is something that needs to be checked while the system is being developed to produce a robust authentication process.
Tampering
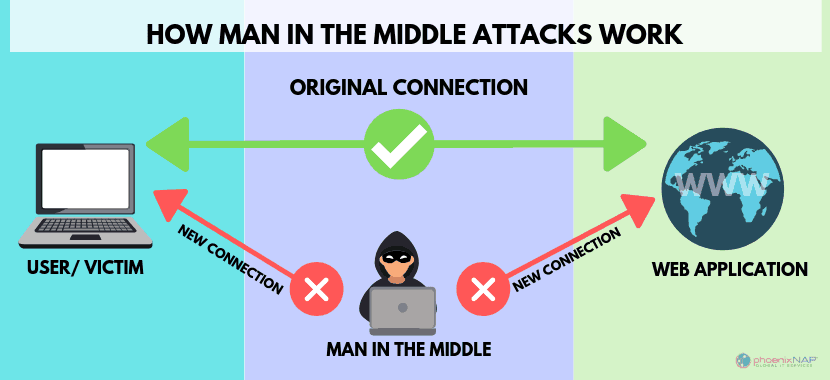
The principle of integrity is violated by tampering. Tampering is the act of modifying user data without the appropriate authorization, whether it be while the data is in transit or while it is stored elsewhere. For example, an MITM attack can lead to tampering. As a result, the development team has to use various countermeasures, such as data encryption in both transit and rest, so that the integrity is not jeopardized.
Repudiation
In repudiation, the attacker erases all signs that can be used to identify them, including deleting system logs. As a result, no one is able to determine what actions were taken or which resources were accessed. Therefore, the development team should undertake thorough logging and monitoring and maintain proper backups.
Information Disclosure
Due to information disclosure, formerly private information is now accessible to the public, such as when the data stored in an S3 bucket is accidentally made accessible to the public. To avoid this, a business ought to make certain that all sensitive data is stored in an appropriate manner with adequate protection when designing the software.
Denial of Service
Denial of service goes against the availability principle. It typically causes a legitimate user from being able to access resources that they should be able to. Such an attack has an impact on an application’s workflow, data storage, and data processing. Therefore, load balancers should be used by the application to address this type of problem.
Elevation of Principle
Elevation of the principle violates the authorization principle. In such a scenario, attackers typically attempt to get privileged access to the software or application, which they then utilize to carry out some unauthorized operations inside the application. To solve these problems, application owners should implement RBAC and multi-tiered authorization.
Conclusion
Choosing a threat classification to use is the initial stage in the process of identifying potential threats. STRIDE is the most widely acknowledged classification. Threat modeling is typically carried out during the beginning stages of product development so that appropriate preventative steps can be implemented while the product is still being developed. It not only reduces costs but also boosts productivity and effectiveness.