The growing popularity of Kubernetes as a container orchestration platform has revolutionized the way we deploy and manage applications. Its versatility and scalability are unmatched, making it a tool to reckon with. However, with these advantages come security challenges. Kubernetes environments can become plagued by vulnerabilities when not managed well, and these vulnerabilities become doorways for attackers to gain unauthorized access.
Kubernetes environments often face an overwhelming list of vulnerabilities, making it challenging to prioritize and address them effectively. This daunting feeling, called CVE shock, is experienced by DevOps and security teams when they are confronted with a significant number of vulnerabilities.
Before we go into dealing with CVE shock, let us understand the different types of risks that contribute to it. The different types of risks within Kubernetes can be broadly classified into 3 types: configuration risks, container vulnerabilities, and API vulnerabilities.
Configuration Vulnerabilities
These vulnerabilities are caused by misconfigurations in the Kubernetes environment. For example, if a user does not properly configure RBAC (role-based access control), an attacker could gain unauthorized access to the cluster.
Container Vulnerabilities
These vulnerabilities are caused by security flaws in container images that are used in Kubernetes clusters. For example, if an attacker is able to compromise a container image, they could inject malicious code into the image so that the new code is executed when the container is started.
API Vulnerabilities
These vulnerabilities are caused by security flaws in the Kubernetes API. For example, if an attacker is able to exploit an API vulnerability, they could gain unauthorized access to the cluster or its resources.
Combat Vulnerabilities & Exposures in Kubernetes Using Kubescape
Given the substantial quantity of vulnerabilities, it is crucial to devise a method for effectively prioritizing and addressing these issues to prevent compromising the Kubernetes system. There are various ways to overcome CVEs and avoid CVE shock. The most common and most effective is using open source tools to identify them effectively and take the necessary actions.
Kubescape, the Kubernetes security tool developed by ARMO, is one such open source tool that provides assistance in effectively dealing with CVE shock. When a developer is faced with a long list of vulnerabilities and exposures, Kubescape helps them organize, prioritize, and target fixing vulnerabilities that threaten their security posture. The main features of Kubescape that help efficiently resolve security issues are as follows:
Efficient Resource Utilization
Kubescape’s scanning process optimizes resource usage by excluding unused libraries and artifacts from the container image. This prevents wasteful efforts being made to patch irrelevant vulnerabilities and saves valuable time and resources.
Relevancy and Prioritization
Kubescape allows you to remove vulnerabilities associated with unused software packages from your list of priorities, enabling you to focus efforts on critical ones. This approach improves efficiency, saving time and resources.
eBPF and Contextual Analysis
Kubescape employs eBPF probes to analyze file activity within running containers. By learning container activity during a designated period, the scanning engine filters the software bill of materials (SBOM) based on accessed files. This results in a more targeted list of vulnerabilities.
Enhanced Security Posture
By prioritizing and promptly addressing relevant vulnerabilities, Kubescape enables organizations to strengthen their security posture, enhance their team’s capacity, and improve their overall bottom line. Focusing on vulnerabilities with actual risks reduces the likelihood of cyberattacks and data breaches.
ARMO’s Approach to Priority Assessment
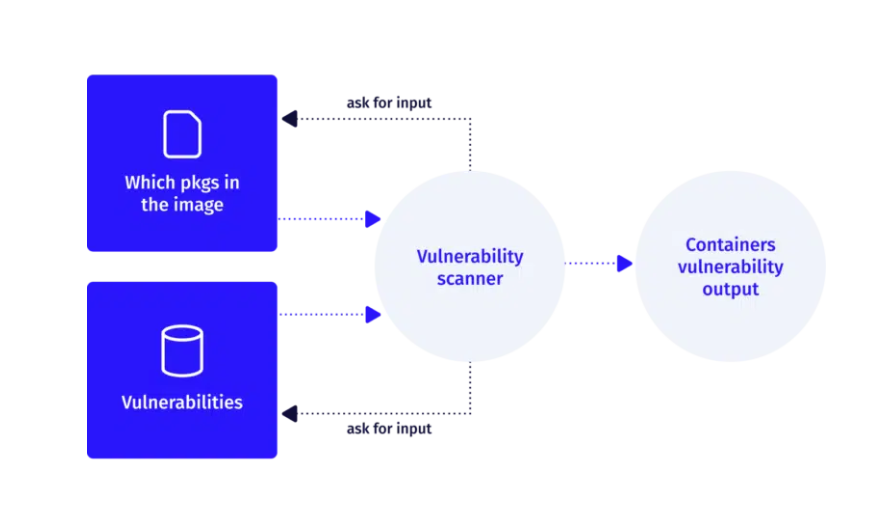
ARMO’s tool, Kubescape, uses a two-pass approach for priority assessment. It works on the principle of culling out the less relevant vulnerabilities and prioritizing the ones that need more urgent attention. These two passes are as follows.
First Pass: The entire list of vulnerabilities, which consists of used and unused code at runtime.
Second Pass: This concise list focuses on the most pertinent vulnerabilities that warrant investigation.
Kubescape provides software bills of materials (SBOM), which are detailed descriptions of all the components, modules, and their dependencies. When a software component is not used during the runtime, it can be removed from the SBOM that is fed into the vulnerability scanner.
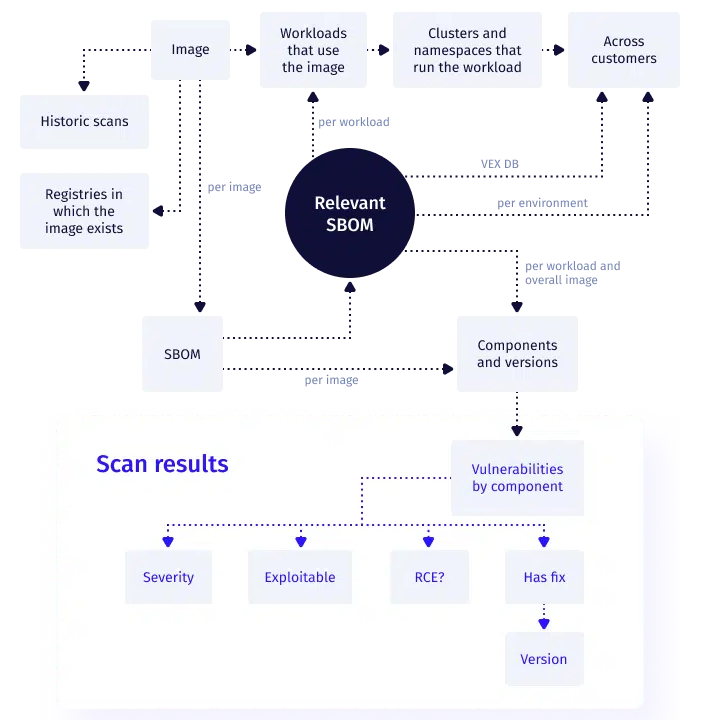
ARMO’s tool introduces a new agent called Taster, which employs eBPF probes to observe the file activity within a live container. As part of the scanning process, Taster generates a software bill of materials (SBOM) that furnishes information about the installed components in the container. When vulnerability checks are performed, we supply the engine with a refined software bill of materials that solely encompasses packages associated with files accessed in the learning period. This enables us to obtain a filtered list of vulnerabilities that are highly likely to be pertinent and relevant.
By adopting this approach, you can implement a more robust strategy that prioritizes critical issues, preventing you from overlooking any crucial areas that require immediate attention.
Steps to Collating Relevant Vulnerabilities with Kubescape
Now that we have understood the broader strokes of Kubescape’s principle functions, let us see it in action. Below is a step-by-step process of how Kubescape arrives at its final list of vulnerabilities that need to be addressed, thus preventing developers from being overwhelmed by issues in a system and suffering CVE shock.
1. Connect the cluster to Kubescape.
2. Go to Repository scanning for detecting vulnerabilities. It uses a CNCF-hosted engine for scanning containers and clusters for misconfigurations and vulnerabilities.
3. When the scanning phase is completed, go to the Vulnerabilities tab, which will provide a management console that directs your attention to the issues that demand immediate focus by leveraging actual usage patterns observed within your own environment.
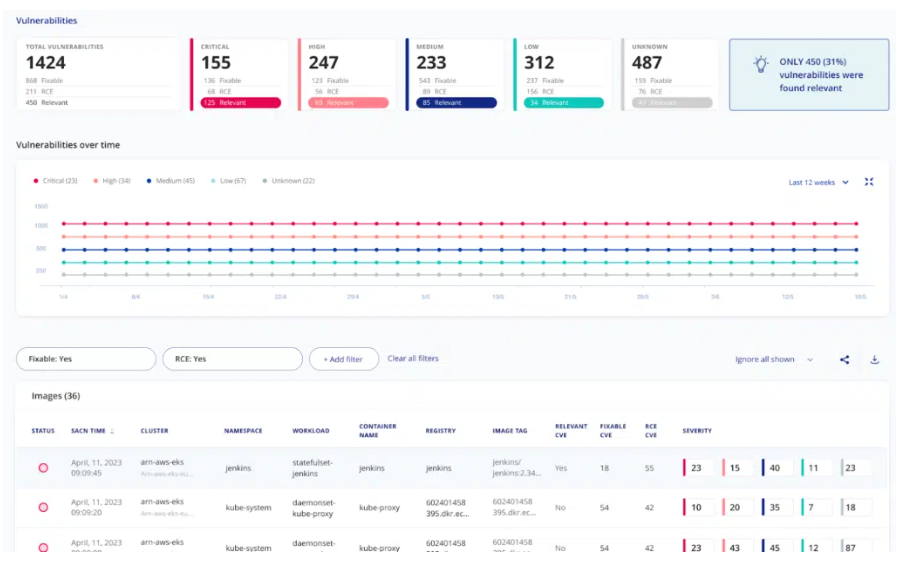
Here, you can analyze the overall count of vulnerabilities and the range of issues spanning from critical to low and focus on the more crucial and relevant vulnerabilities among them. The console’s bottom table furnishes you with detailed information regarding the vulnerabilities that need to be addressed.
Conclusion
In conclusion, prioritizing Kubernetes security is paramount in today’s digital landscape where containerized environments are increasingly prevalent. As organizations embrace the benefits of Kubernetes for scalability and agility, it becomes crucial to address vulnerabilities promptly and effectively. Kubescape provides invaluable assistance in tackling Kubernetes vulnerabilities by offering advanced features and capabilities, enabling organizations to confidently harness the power of Kubernetes while maintaining a robust and secure infrastructure.